41 | Add to Reading ListSource URL: eits.uga.eduLanguage: English - Date: 2015-10-21 16:49:33
|
|---|
42 | Add to Reading ListSource URL: www.digitalcatapultcentre.org.ukLanguage: English - Date: 2016-03-09 06:12:58
|
|---|
43 | Add to Reading ListSource URL: norbert-pohlmann.comLanguage: English - Date: 2015-11-20 14:35:18
|
|---|
44 | Add to Reading ListSource URL: www.identrust.comLanguage: English - Date: 2014-05-01 19:01:13
|
|---|
45 | Add to Reading ListSource URL: campaign.axisbank.comLanguage: English - Date: 2015-05-05 08:51:11
|
|---|
46 | Add to Reading ListSource URL: www.winlab.rutgers.eduLanguage: English - Date: 2013-04-18 23:09:49
|
|---|
47 | Add to Reading ListSource URL: www.susecon.comLanguage: English - Date: 2015-11-20 11:18:31
|
|---|
48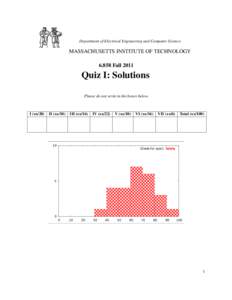 | Add to Reading ListSource URL: css.csail.mit.eduLanguage: English - Date: 2016-01-29 11:50:05
|
|---|
49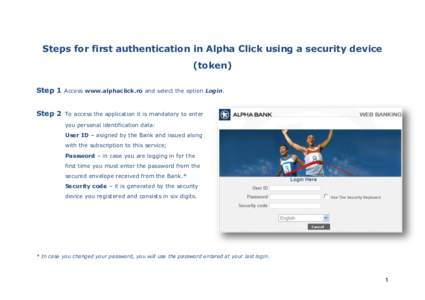 | Add to Reading ListSource URL: www.alphaclick.ro- Date: 2014-03-26 08:36:50
|
|---|
50 | Add to Reading ListSource URL: www.ijmetmr.comLanguage: English - Date: 2015-06-22 08:29:01
|
|---|